User Access Control Prevent Unauthorized Access to Systems and Applications
Overview
You need to prevent unauthorised use of your webapp.
Systems and applications can be hacked in a variety of ways but one of the most common points of entry is via logins that do not have sufficient security procedures in place.
Potential hacks include the brute force password hack which exploits the use of weak passwords, key loggers which capture passwords as the user is entering them and phishing scams whereby the user is tricked into providing a password to a malicious third party.
Strengthening login security should therefore be a priority for all organisations.
Two-Factor (Multi-Factor) Authentication
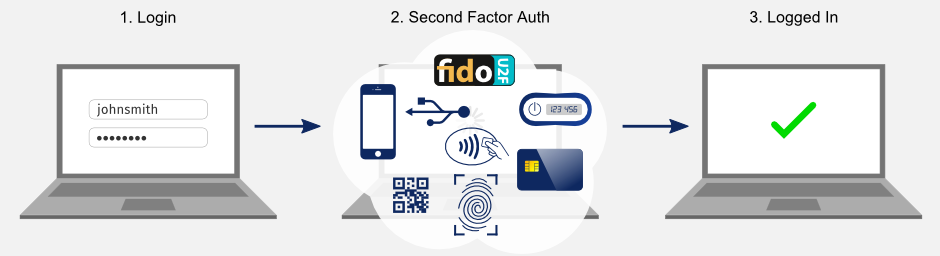
Logins are strengthened by adding a second step to the login procedure. The second factor can be something the user has (eg, their smartphone or a dongle) or who they are which is assertained via biometrics. Combining something they have with something they know is the essence of two-factor authentication.
By making the process as simple as possible and providing a selection of authentication methods, the user experience is improved. This leads to better user acceptance of strong authentication.
Management
With your application secured so only legitimate users can use it, you can now manage your users and the devices assigned to them. Take control of your security by managing the lifecycle of users and their authentication tokens. For example, if an exployee leaves your company, you can revoke their authentication device and block their login. This is a broader topic known as Identity & Access Management which is covered here.
